MOVING UP MARKET WITH AXIOM
Though features outlined on pages 2 and 3 are covered by the RBH Integra32 Security Management System, additional features are available by upgrading to the RBH Axiom Security Management System.
Multi-site Systems with Both Central and Local Management
Managing multiple sites? Want to reduce local on-site presence or just add a fall back option for customer service and added security? Combine your properties with the AxiomV based command center or make it an accessible tool for central security office staff.
- • Global access and management from main office.
- • Local management access restricted to people and equipment on designated site only.
- • Access to high end features even at small sites: software package is shared, reducing initial costs.
Web Based Management
Direct control by administration via Web browser (Safari, IE, Firefox, Chrome and many others)
Create limited accounts for site management use:
• Add / delete cards
• Change access and unlocking schedules
• Produce reports
• Override doors remotely
Asset Tracking
To prevent theft of your organization’s assets, our Integrated Asset Tracking system is designed to help stop valuables from being removed from the premises if they are not authorized to.
Our fully integrated database will track each asset as it moves about the facility. If the asset moves to a place it is not authorized, our system is then able to notify authorities of an attempted theft and if needed will lock down doors to prevent an asset from leaving the premises.
Additional Parking Controls
• Counting of available parking spots, “Full” sign operation.
• Allow only a limited number of parking uses.
• Advanced Anti-passback functionality with “drive through” interlock.
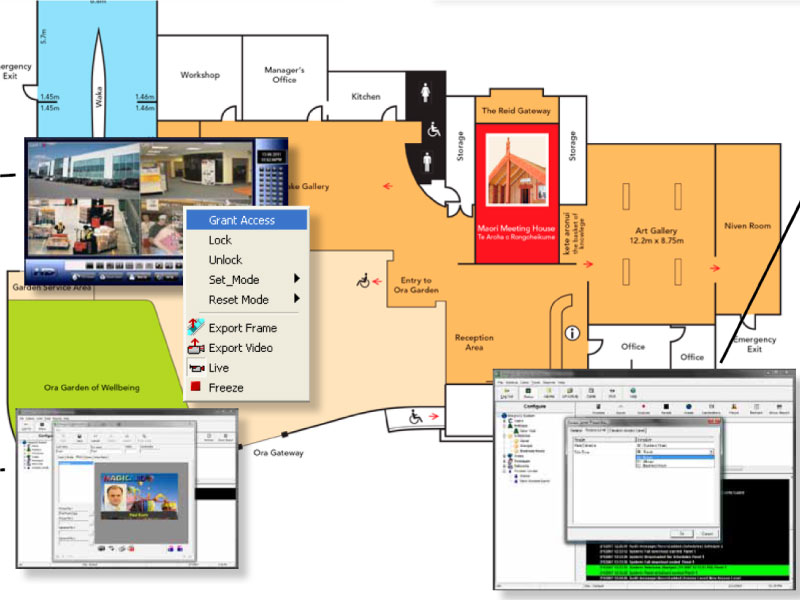
Mapping
Helps security contractors to familiarize themselves with
your system quicker
• Control doors and monitor alarms directly from the map
• Touch screen compatible
Visitor Management
• Seamlessly integrate with popular EasyLobby visitor
management system
• Use built in optional functionality
SECURING ACCESS TO THE SITE
Making sure that only the authorized personnel have access to the restricted areas of a museum can be challenging. RBH access contol solutions can offer complete control of employees and visitors.
Visual Verification
As people use cards or transmitters RBH software can pull up a picture on file of a person assigned to that card.
• Added security – address stolen card issues
• Train security personnel to recognize employees visually
• Help with greeting
Email/Text Message Notification
Someone’s card is not working, or a door is left propped open – know about it instantly with the help of a cell phone, tablet or a computer.
Access to the Building
Getting into a building should be a simple experience for authorized people: employees, janitorial staff, contractors and visitors can be covered:
• Proximity key tags (fobs) and cards
• Proximity enabled car transmitters
• Adhesive proximity labels for cell phones
• In addition, you can use: code keypads, fingerprint readers and many other technologies supported by RBH
Video Integration
Pop up live video automatically, for example – someone’s card is not working, verify their identity and then open the door. Automate event review – history reports are linked to recorded video
Video history trail
Every event (door opening, door open too long, etc.) can generate a video pop-up or a single click playback of the event when integrated with a Digital Video Recorder (DVR), Network Video Recorder (NVR), or a Video Management System (VMS).
Access Control
Employee-only or off-hours areas will keep out patients and visitors, while providing easy access for doctors, nurses and the supporting staff:
- • Proximity Photo IDs
- • PIN Keypads
- • Iris Recognition Readers
- • In addition, you can use fingerprint readers and many other technologies supported by RBH
Event driven video integration
• Link a door activity to specifi c cameras
• Use your CCTV system as door bell
• Automate event playback
Photo ID
Create graphic IDs for your employees as well as frequent visitors and contractors. Just add a camera and a printer.
Mantraps/Sally Ports
Keeping only a single door open at a time in a security vestibule is built into our controllers:
• No more relays, interlock wiring and timers
• Standard access control door wiring
• Any technician can understand, install and service
• A single check mark (“Enable interlock”) in configuration of a 2-door access controller joins its doors in Mantrap logic
interlock.
Two Man Rule
The two-man rule is a control mechanism designed to achieve a high level of security for especially critical material
or operations. Under this rule all access and actions requires the presence of two authorized people at all times.
MONITOR PRICELESS INVENTORY
Security issues can arise almost anywhere. To address them proactively, it is important to set up appropriate access and monitoring policies, and ensure easy access to reporting and playback for speedy investigations
Anti-passback
When the antipassback feature is enabled, cardholders must present their card for entry to and exit from all areas.
Antipassback prevents a cardholder from using his/her card twice at the same access point. It also provides an important employee management feature, as the access system can provide information regarding how many people are within a building or access controlled area at a specific time, as well as their identities.
Event Dependent Access
In order to gain access to a specified door, first the user must have passed through another specified door. For example; the user must enter the clean room prior to handling artwork in the storage area. If the system does not have a record of an entrance and exit from the clean room that user will be denied access to the storage area.
Control at the Door
Control at the Door
Delivery, a special event, cleaning or remodeling of a common area, changes to lock/unlock and lock out functions are normally controlled from a computer, requiring management to be on site. RBH allows this control at the door and by specifically designated people:
With proximity or fingerprint readers:
• 2-Swipe – present your card or finger twice in a row and lock-unlock doors as needed for deliveries and special events for example. Need to lock gym before it is
scheduled to lock automatically? – Double swipe!
• 4-Swipe - present your card or finger 4 times in a row and lock residents out of an area with wet floors or unsafe conditions. Another 4-swipe and everything goes
back to normal mode of operation.
• 3, 5-swipe – automate anything: unlock all elevator floors, turn on/off lights or equipment, and an uncounted number of other options are at your command
With proximity reader with built in keypad:
Swipe your valid card or enter your security PIN, followed by an action code – depending which code you use as specific
command will be issued. You can do anything covered by 2,3,4,5-swipe functions.
Different access levels for different employees
Not every employee needs to have access to every area of your facility. Set up acess levels to allow only the employees that need to be there, when they need to be there.
• Set who is allowed to go where and when
• Have an audit trail
• Link it to video recording for easy incident investigations
Disposable Codes
Create a single use or a single/multi-day code that can be given to delivery or other contractors.
• No need for keys
• Can’t forget to return them
• Audit trail of use
• Limiting permitted hours of work
Event Log
Know who was where and when, flexible history reports make it easy